Most websites rely on first and third party tags/scripts for various business needs - collecting analytics data, delivering ads, running A/B tests, and verifying credit cards. But these tags carry a lot of risk.
Recent data breaches caused by compromised tags at British Airways, Newegg, Ticketmaster, and others have caused new scrutiny to be applied to content that is placed on a website, especially from third party vendors.

What’s happening?
Hackers are injecting malicious skimming code into website tags. The malicious code watches for Personally Identifiable Information (PII), like credit card numbers, and starts skimming the data and sending it to another domain.
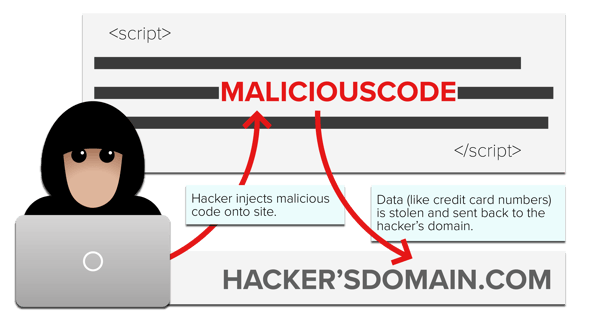
Now let’s consider the recent set of data breaches and discuss how they could have been prevented.
British Airways
Payment page JavaScript code was compromised, sending names and credit card numbers to another domain.
Ticketmaster
The Sociaplus JavaScript tag was hacked. Credit cards were skimmed and sent to another domain.
Newegg
Compromised JavaScript on the payment page skimmed credit card data and sent the data to the hacker’s well-disguised domain, neweggstats.com.
In each case, malicious code made it onto the site, personal data was collected by that code, and then data was sent to the hacker’s domain.
In response to the threat, some sites are stripping down their tags and even sacrificing some of the power that their third party services are providing. This reduces the risk of skimming-related data breaches but does not eliminate the threat.
Any tag can be compromised, especially one from a third party.
The solution
You need to lock down your site without sacrificing the benefits of your first and third party tags.
This can be done through a Content Security Policy (CSP) – a browser security standard that ensures only whitelisted first and third party domains are allowed to load on your site. So, if one of your tags is compromised, data will not be sent to a domain that isn’t whitelisted.
Creating and managing a CSP is incredibly complex. Despite its compatibility with all major browsers, only 0.38% of the Alexa 1M Top Sites have one.
The reason for this complexity is that most sites have dozens or even hundreds of third party providers on their site. Each provider has multiple domains (some >100), and those domains change from time to time, creating an administrative nightmare.
Blue Triangle solves this administrative nightmare with CSP Manager: A comprehensive approach to monitoring and regulating first and third party activity.
How CSP Manager Works
Step 1: Data Collection
We combine Real User Monitoring (RUM) with Synthetic Monitoring (automated web page measurements from real browsers) to identify what first and third party domains are loading on your site, who owns them, and what pages they are loading on.
Step 2: Create Domain Whitelist
Now that you know what domains are currently loading on your site, each of your vendors completes a Service Security Application where they list every domain they are currently using, whether the domain is present on your site or not.
This automated process creates a domain whitelist that will exist in your CSP.
Step 3: Approve Whitelist & Generate CSP
Tag and security teams approve those whitelisted domains inside Blue Triangle.
Once approved, Blue Triangle automatically generates a detailed and comprehensive CSP that you can deploy on your site.
Step 4: Deploy CSP & Prevent Malicious Activity
As soon as the CSP is deployed, the CSP will block any unknown or malicious domain that appears on your website. If a new domain appears, Blue Triangle will send you an alert.
The process and automation we built with CSP Manager makes locking down your site easy to set up and administer.
This process blocks many types of malicious behavior and locks down your site. It also can prevent certain types of client-side spyware from adding pop-ups to your page and “hijacking” your user sessions.
Summary
If you are running your site today without a comprehensive Content Security Policy (CSP), you are vulnerable, or in Star Trek terminology, “Running with your shields down.”
Blue Triangle can help you with process and automation to build and maintain your CSP in a way that is not error prone.
Interested in learning more?

During the holiday rush, every shopper matters
Optimize the customer journey before the eCommerce event of the year.



