"We have too many tags to manage."
Recently I was on the phone with an eCommerce site owner that used the term “wild west” when describing the chaos and lack of control of their first and third party tags.
Here's a site with 61 first and third party tags:
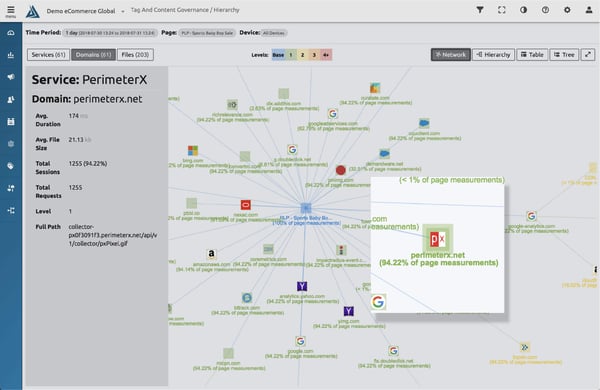
This lack of tag control has led to data breaches of personally identifiable information (PII), like credit card numbers. The sad truth is that our online shopping is not as secure as it should be.
While you can’t run a site without analytics, advertising, retargeting, and product feedback services, you can’t let those tags go unmonitored and unchecked. The recent breaches at British Airways, Ticketmaster, and Newegg are clear examples of the flaws in how people currently manage their tags.

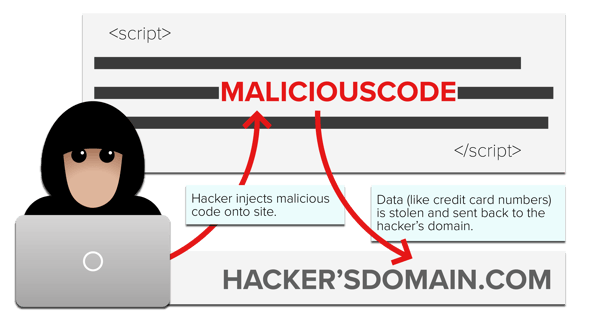
The Magecart hacking group was able to inject small amounts of malicious code via first or third party JavaScript tags.
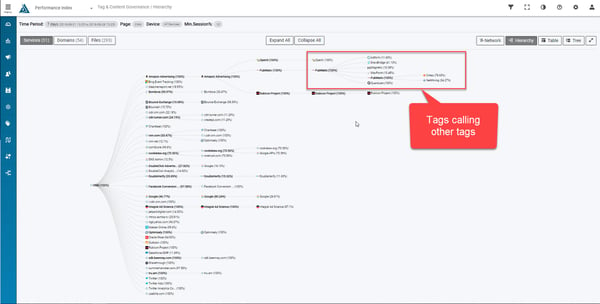
That said, first and third party tags need a way to get on the site to perform the tasks they are designed to do. You can add them directly to pages, through tag managers, or dynamically with another tag.
Third party tags can add additional tags dynamically too, which can be wanted or unwanted. This is called “piggy-backing”. In a perfect world, piggy-back tags would always be accounted for, but they’re often forgotten, or added without consent or approval. In turn, these piggy-back tags can add even more piggy-back tags -- and you have to hope that none of these services contain anything malicious.
This "wild west" eCommerce environment has created the perfect opportunity for hackers to exploit and add “form jacking” code to one of the first or third party tags loading on the site. Virtually any code added to the site could get exploited by hackers for the purpose of skimming credit cards off to unauthorized domains. Your site is at risk unless you have safeguards on the site to prevent your pages from communicating with new and unauthorized destinations (domains) on the internet.
It is common practice to do occasional risk assessments on your tag library. While this is a necessity, your site remains unguarded for the majority of the year.
A quick fix is not the answer.
While a well implemented content security policy (CSP) could solve this issue on your site, it could leave your site crippled if not managed and updated regularly with your current content and services.
In order to create a CSP, you have to first compile a list of all first and third party services and the tags, domains, and files they use on your site. This would be difficult for just one page of a website, but most sites load different services on different pages. Some third party services have several domains required to operate correctly.
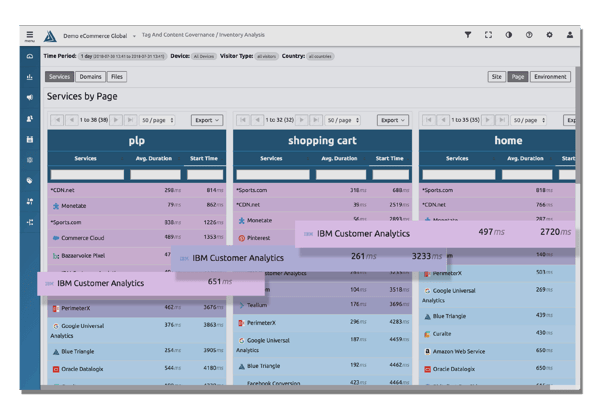
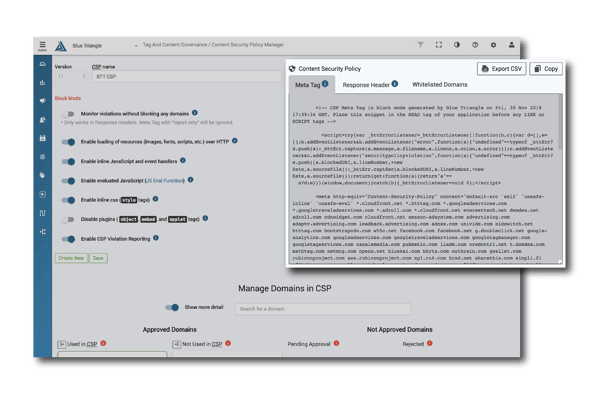
Blue Triangle’s Content Security Policy Manager takes over the automation of this process so your site can stay secure and up to date.
With Blue Triangle's CSP Manager, someone from your team will be notified whenever a new domain is added to your site. In order for this service to function, someone from your security team will have to approve the tag. Newegg’s customers information was skimmed through a domain injected onto their site called neweggstats.com. With Blue Triangle you can make sure this never happens on your site.
Why Blue Triangle?
Blue Triangle's CSP Manager provides the automation and central repository to automatically detect all of your active vendors and their respective domain traffic. Your new CSP locks down your site and continues to protect against data breaches.
- Automation for information gathering
- Integrated and up-to-date tag library
- Approval process for 1st and 3rd party domains
- First-class CSP automation

During the holiday rush, every shopper matters
Optimize the customer journey before the eCommerce event of the year.